Cisco IOS on UNIX (IOU) is a fully working version of IOS that runs as a user mode UNIX/LINUX process. IOU is built as a native system image and run just like any other program. IOU supports all platform independent protocols and features.
With regard to functionality, it is very similar to GNS3 but it does not require nearly the resources that several virtual routers running under dynamips does.
IOU allows you to build out a network topology on a single PC without the need for physical routers. This is useful for validating network designs, proof-of-concept testing, and certification self-study.
Legal Warnings
If you are not an authorized Cisco employee (or trusted partner), usage of Cisco IOU is prohibited. From an old, internal-only Cisco web page:
Cisco IOS on Unix is a tool intended for internal use only. Distribution of IOU images to customers or external persons, or discussion of IOU with customers or external persons, is prohibited. Don’t do it or we’ll have to come and kill you.
Cisco IOU, just like IOS, is copyrighted software that belongs to cisco Systems, Inc. Distribution of copyrighted software is a federal crime in the United States. I cannot speak regarding the laws of other countries.
In addition, any requests for Cisco IOU images in the comments section of this blog will be deleted, regardless if distribution is legal in your country.
Installing and Running IOU
Checking the Distro
$ cat /etc/issue
Ubuntu 11.04 \n \l
Checking the CPU
$ uname -a
Linux ltsp180 2.6.38-13-generic #55-Ubuntu SMP Tue Jan 24
15:34:24 UTC 2012 x86_64 x86_64 x86_64 GNU/Linux
Installing 32 bit Libs on a 64 bit Distro
$ sudo apt-get install ia32-libs
Installing BBE
$ sudo apt-get install bbe
OR
http://packages.ubuntu.com/
- Your distro | Editors | BBE
Download the file (bbe\_0.2.2-1\_i386.deb)
And install it manually
$ sudo dpkg -i bbe_0.2.2-1_i386.deb
Installing and Linking the "libcrypto" Library
You either do not have libssl installed or your version is much newer than what Cisco has linked against when building the IOU images.
First, ensure that libssl is installed. On Debian and Ubuntu:
$ sudo apt-get install libssl0.9.8
Next, youll need to make a symbolic link pointing to the "libcrypto.so.4" file that IOU is looking for.
On 32-bit distros:
$ sudo ln -s /usr/lib/libcrypto.so.0.9.8 /usr/lib/libcrypto.so.4
On 64-bit distros:
$ sudo ln -s /usr/lib32/libcrypto.so.0.9.8 /usr/lib32/libcrypto.so.4
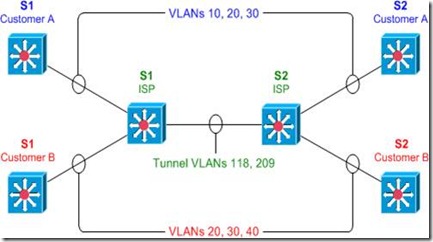
NETMAP File
The network topology map, or NETMAP, file describes the topology of your virtual network. It is used for controlling the layout of the virtual cabling. If you have used dynagen, this is the equivalent of the .net file.
NETMAP
----------------
100:0/0 200:0/1
The above netmap file means that you are connecting port 0/0 of router 100, to port 0/1 of router 200:
[Router 100]--Ethernet 0/0------Ethernet 0/1--[Router 200]
Checking the Hostname For the "iourc" File
$ hostname -s
chaos
The "iourc" File
iourc
-------------------------
[license]
chaos = 4C5556554353434F;
The IOURC file is a configuration file for Cisco IOU. Cisco IOU looks in this file for your license key at startup.
Note: The method below for patching the IOU image for your machine's hostname, implies that, the license is "4C5556554353434F" and the only change is the hostname.
Giving Execution Permitions to the IOU Image
$ chmod +x i86*
Executing the IOU Image For Router 100 - Non Patched
$ ./i86bi_linux-adventerprisek9-ms.151-4.M 100
***************************************************************
IOS On Unix - Cisco Systems confidential, internal use only
Under no circumstances is this software to be provided to any
non Cisco staff or customers. To do so is likely to result
in disciplinary action. Please refer to the IOU Usage policy at
wwwin-iou.cisco.com for more information.
***************************************************************
IOU License Error: invalid license
License for key 7f030f required on host ?chaos?.
Obtain a license for this key and host from the following location:
http://wwwin-enged.cisco.com/ios/iou/license/index.html
Place in your iourc file as follows (see also the web page
for further details on iourc file format and location)
[license]
chaos = <16 char license>;
This attempt didn't work because the IOU image hasn't been patched for your hostname
Patching IOU Image For Key "4C5556554353434F"
$ for F in i86bi_linux-*;do bbe -b "/\xfc\xff\x83\xc4\x0c\x85\xc0\x75\x14\x8b/:10"
-e "r 7 \x90\x90" -o $F.x $F;mv $F.x $F;done;chmod +x ./i86bi_linux-*
Note: This works for the following IOU images (didn’t worked for Layer 2 Images):
- i86bi_linux-adventerprisek9-ms
- i86bi_linux-ipbase-ms
For the i86bi_linuxl2-upk9-ms, you need to use something like IOUGEN.
Executing the IOU Image For Router 100 - Patched IOU $ ./i86bi_linux-adventerprisek9-ms 100
***************************************************************
IOS On Unix - Cisco Systems confidential, internal use only
Under no circumstances is this software to be provided to any
non Cisco staff or customers. To do so is likely to result
in disciplinary action. Please refer to the IOU Usage policy at
wwwin-iou.cisco.com for more information.
***************************************************************
Port 0 is not connected to anything
Restricted Rights Legend
Use, duplication, or disclosure by the Government is
subject to restrictions as set forth in subparagraph
(c) of the Commercial Computer Software - Restricted
Rights clause at FAR sec. 52.227-19 and subparagraph
(c) (1) (ii) of the Rights in Technical Data and Computer
Software clause at DFARS sec. 252.227-7013.
cisco Systems, Inc.
170 West Tasman Drive
San Jose, California 95134-1706
Cisco IOS Software, Linux Software (I86BI_LINUX-ADVENTERPRISEK9-M),
Version 15.1(4)M, DEVELOPMENT TEST SOFTWARE
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2011 by Cisco Systems, Inc.
Compiled Fri 25-Mar-11 16:44 by prod_rel_team
This product contains cryptographic features and is subject to United
States and local country laws governing import, export, transfer and
use. Delivery of Cisco cryptographic products does not imply
third-party authority to import, export, distribute or use encryption.
Importers, exporters, distributors and users are responsible for
compliance with U.S. and local country laws. By using this product you
agree to comply with applicable laws and regulations. If you are unable
to comply with U.S. and local laws, return this product immediately.
A summary of U.S. laws governing Cisco cryptographic products may be found at:
http://www.cisco.com/wwl/export/crypto/tool/stqrg.html
If you require further assistance please contact us by sending email to
export@cisco.com.
Warning: the compile-time code checksum does not appear to be present.
Linux Unix (Intel-x86) processor with 140260K bytes of memory.
Processor board ID 2048042
8 Ethernet interfaces
8 Serial interfaces
64K bytes of NVRAM.
Executing the IOU Image For Router 200 - Patched IOU $ ./i86bi_linux-adventerprisek9-ms 200
***************************************************************
IOS On Unix - Cisco Systems confidential, internal use only
Under no circumstances is this software to be provided to any
non Cisco staff or customers. To do so is likely to result
in disciplinary action. Please refer to the IOU Usage policy at
wwwin-iou.cisco.com for more information.
***************************************************************
Port 0 is not connected to anything
Restricted Rights Legend
Use, duplication, or disclosure by the Government is
subject to restrictions as set forth in subparagraph
(c) of the Commercial Computer Software - Restricted
Rights clause at FAR sec. 52.227-19 and subparagraph
(c) (1) (ii) of the Rights in Technical Data and Computer
Software clause at DFARS sec. 252.227-7013.
cisco Systems, Inc.
170 West Tasman Drive
San Jose, California 95134-1706
Cisco IOS Software, Linux Software (I86BI_LINUX-ADVENTERPRISEK9-M),
Version 15.1(4)M, DEVELOPMENT TEST SOFTWARE
Technical Support: http://www.cisco.com/techsupport
Copyright (c) 1986-2011 by Cisco Systems, Inc.
Compiled Fri 25-Mar-11 16:44 by prod_rel_team
This product contains cryptographic features and is subject to United
States and local country laws governing import, export, transfer and
use. Delivery of Cisco cryptographic products does not imply
third-party authority to import, export, distribute or use encryption.
Importers, exporters, distributors and users are responsible for
compliance with U.S. and local country laws. By using this product you
agree to comply with applicable laws and regulations. If you are unable
to comply with U.S. and local laws, return this product immediately.
A summary of U.S. laws governing Cisco cryptographic products may be found at:
http://www.cisco.com/wwl/export/crypto/tool/stqrg.html
If you require further assistance please contact us by sending email to
export@cisco.com.
Warning: the compile-time code checksum does not appear to be present.
Linux Unix (Intel-x86) processor with 140260K bytes of memory.
Processor board ID 2048042
8 Ethernet interfaces
8 Serial interfaces
64K bytes of NVRAM.
If you dont need/want to have access to the equipments via network (telnet) this is enough, for you, add a couple more equipments and connections to the NETMAP file you are good to go.
IOU Image Options ./i86bi_linux-adventerprisek9-ms Usage: <image> [options] <application id>
<image>: unix-js-m | unix-is-m | unix-i-m | ...
<application id>: instance identifier (0 < id <= 1024)
Options:
-e <n> Number of Ethernet interfaces (default 2)
-s <n> Number of Serial interfaces (default 2)
-n <n> Size of nvram in Kb (default 16KB)
-b <string> IOS debug string
-c <name> Configuration file name
-d Generate debug information
-t Netio message trace
-q Suppress informational messages
-h Display this help
-C Turn off use of host clock
-m <n> Megabytes of router memory (default 128MB)
-L Disable local console, use remote console
-u <n> UDP port base for distributed networks
-R Ignore options from the IOURC file
-U Disable unix: file system location
-W Disable watchdog timer
-N Ignore the NETMAP file
NVRAM Files The IOU instances on the above example created the following files:
- nvram_00100 -->Router 100
- nvram_00200 -->Router 200
as you migth recall the nvram, is the were the startup-config is stored so these files are more or less the startup config for router 100 and 200.
If you type:
$ cat nvram_00100
????
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname Router100
!
boot-start-marker
boot-end-marker
<...>
you can see the startup-config, plus a bit off jiberish.
TSHOOT - Cisco IOU Error Messages
- What does ``UNIX ERR:tcgetattr:Invalid argument''mean? Im not sure, honestly, but it doesnt seem to hurt anything or cause any loss of functionality. It appears that it can be safely ignored.
- i86bi_linux_adventerprisek9-ms: No such file or directory Youre probably running a 64-bit version of Linux. On Debian and Ubuntu, installing the ia32-libs package will fix this for you (for other distros, youre on your own):
$ sudo apt-get install ia32-libs
- i86bi_linux_adventerprisek9-ms: error while loading shared libraries You either do not have libssl installed or your version is much newer than what Cisco has linked against when building the IOU images.
First, ensure that libssl is installed. On Debian and Ubuntu:
$ sudo apt-get install libssl0.9.8
Next, youll need to make a symbolic link pointing to the libcrypto.so.4 file that IOU is looking for.
On 32-bit hosts:
$ sudo ln -s /usr/lib/libcrypto.so.0.9.8 /usr/lib/libcrypto.so.4
On 64-bit hosts:
$ sudo ln -s /usr/lib32/libcrypto.so.0.9.8 /usr/lib32/libcrypto.so.4
- Im getting a host not found in iourc file error message. Use the correct hostname in your IOURC file. See above.
- How can I Add an NM-16ESW module? You cant.
- Oh, come on! There Must be Some Way to add ATM or NM-16ESW modules! Nope.
- Wrapper-linux: No such file or directory error message.
Provide the correct path to the IOU image as the -m option. If it is in the current directory, refer to it as ./i86bi_linux-adventerprisek9-ms, for example.
- Ive tried everything and I cant get it to work. What should I do? Use GNS3 instead.
- Will you send me a copy ? No. In addition, if you post any comments below asking for or offering IOU images, they will be deleted whenever I see them.
Wrapping the IOU Image Execution for Telnet Access
Wrapper - What it is And How It Works
When you start up an IOU router from the command-line, it will stay in the foreground and youll be connected to the console. This may not always be the desired behavior, especially if you wish to telnet to the console from another host on the network (similar to dynamips).
The wrapper program can be used to redirect a TCP port to the console of the router so that you can do exactly this.
How do I use the Wrapper
$ ./wrapper
Usage: ./wrapper [-v] -m<image name> -p<port number> -- [iou options] <router ID>
where <port number> is in the range <1024-65550>
all options after the '--' are passed to iou
[-v] Display version
For example, instead of just running ./imagename <application id>, you would use something like this:
$ ./wrapper -m ./imagename -p 2000 -- -e0 -s1 -m 64 100
This would instruct the wrapper to startup the IOU image named ./imagename and listen on TCP port 2000. Any options after the double-hyphen (-) are passed off to the IOU image so, in this case, our IOU instance would start up with zero Ethernet interfaces (-e0), one serial interface (-s1), which actually means four serial interfaces in newer images, due to a feature called “Wide Port Adapters'', and 64 MB of RAM (-m 64).
The “Application ID”, which we'll use to refer to this instance in the NETMAP file (see above), is 100.
The wrapper is most useful in a shell script to start up and background a number of IOU instances at once. For a complete example showing a NETMAP file and a corresponding shell script to startup all IOU instances, see my article iou2net.pl, an IOUlive replacement:
- http://evilrouters.net/2011/09/22/iou2net-pl-ioulive-replacement-netmap-startup-script/
Stopping the IOU's When Using the Wrapper
If you are using the wrapper and have background the IOU instances, you'll need to find the process ID of the instance you want to stop and use the kill command.
To see all of your running IOU instances, use this command:
$ ps -ef | grep [w]rapper
Find the instance you want to stop and pass the corresponding process IDs to the kill command.
To stop all running IOU instances in a single fell swoop, use the following:
$ ps -ef | grep [w]rapper | awk '{ print $2 }' | xargs kill
Executing the IOU Image For Router 100 - via Wrapper
$ ./wrapper-linux -m ./i86bi_linux-adventerprisek9-ms -p 2100
-- -e3 -s3 -m 128 -n 16 100 > /dev/null 2>&1 &
Command Dissected:
-m ./i86bi_linux-adventerprisek9-ms - Wrapped IOU Image
-p 2005 - Wrapper's telnet port for remote access
-- - IOU image options
-e3 - 3 ethernet interfaces (in some IOU is 3x4)
-s3 - 3 ethernet interfaces (in some IOU is 3x4)
-m 128 - Megabytes of router memory (default 128MB)
-n 64 - Size of nvram in Kb (default 16KB)
100 - IOU router id on the NETMAP file > /dev/null 2>&1 - Redirecting the STDOUT and STDERR into the null file (blackhole) & - Running the wrapper in background
$ telnet localhost 2100
Trying 127.0.0.1?
Connected to localhost.
Escape character is ?^]?.
?- System Configuration Dialog ?-
Would you like to enter the initial configuration dialog? [yes/no]:
% Please answer ?yes? or ?no?.
Executing the IOU Image For Router 200 - via Wrapper
$ ./wrapper-linux -m ./i86bi_linux-adventerprisek9-ms -p 2200 -- -e3 -s3 -m 128 -n 16 200 > /dev/null 2>&1 &
Command Dissected:
-m ./i86bi_linux-adventerprisek9-ms - Wrapped IOU Image
-p 2005 - Wrapper's telnet port for remote access
-- - IOU image options
-e3 - 3 ethernet interfaces (in some IOU is 3x4)
-s3 - 3 ethernet interfaces (in some IOU is 3x4)
-m 128 - Megabytes of router memory (default 128MB)
-n 64 - Size of nvram in Kb (default 16KB)
100 - IOU router id on the NETMAP file > /dev/null 2>&1 - Redirecting the STDOUT and STDERR into the null file (blackhole)
& - Running the wrapper in background
$ telnet localhost 2100
Trying 127.0.0.1?
Connected to localhost.
Escape character is ?^]?.
?- System Configuration Dialog ?-
Would you like to enter the initial configuration dialog? [yes/no]:
% Please answer ?yes? or ?no?.
Note: This example is same as the one above but via wrapper and some IOU options.
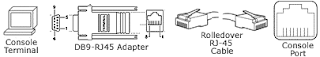
Connecting IOU to the Real World
The are several options:
Graphical Interfaces
There are at least two that I know about:
Now IOU is supported on GNS3, check out how to set it up here:
Based On:
![[Multicast-realdemo.jpg]](https://blogger.googleusercontent.com/img/b/R29vZ2xl/AVvXsEgy8TnjoKFrLE-jDL5MEBuH_eO1JyEf_oWoRDOlZqcFY_ylBT9TsJRgVD9GH6L01718rwsC51K2bFFQqzrRWzrKuhF3b-eSn6oCKf4KOpZrnTLTFhsl50Hu79Yn09egyxfnmkhIfILqUXwB/s1600/Multicast-realdemo.jpg)