Have you ever wanted to reach a server via some application, for example ssh, but you couldn’t because the remote computer (LinuxB) was beind NAT, and you didn’t had access to the router (CPE2-NAT) to add a port forwarding:
but if you add another server with a Public IP (LinuxM) in the midlle you can set up a Reverse SSH Tunel between the destination (LinuxB) and the server in the middle (LinuxM) that will forward conection to a local port on LinuxM to the destination port on LinuxB via the established ssh session that has the reverse/remote tunel configured.
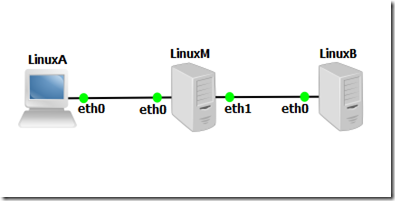
To test the Reverse SSH Tunel to bypass NAT I’m going to do a proof of concept (POC), with some linux (Ubuntu) machines with private addressing, the cenario looks like this:
Linux_M – Middleman
===========================================================
## Hostname ##
sudo nano /etc/hostname
LinuxM
hostname LinuxM
hostname
sudo nano /etc/hosts
127.0.1.1 LinuxM
## Interfaces ##
sudo ifdown eth0
sudo ifconfig eth0 192.168.1.254 netmask 255.255.255.0
sudo ifup eth0
sudo ifdown eth1
sudo ifconfig eth1 172.16.1.254 netmask 255.255.255.0
sudo ifup eth1
## IP Forwarding (Routing) ##
sudo sysctl -w net.ipv4.ip_forward=1
## Activate Gateway Ports ##
sudo nano /etc/ssh/sshd_config
GatewayPorts yes
sudo service ssh stop
sudo service ssh start
#####################################################
# When you forward a TCP port (either locally or
# remotely), by default SSH only listens for
# connections to the forwarded port on the loopback
# address (localhost, 127.0.0.1). This means only
# other programs running on the same host as the
# listening side of the forwarding can connect to
# the forwarded port. This is a security feature,
# since there is no authentication applied to such
# connections. Also, such a forwarded connection is
# potentially insecure, since a portion of it is
# carried over the network in a plain TCP connection
# and not protected by SSH.
#####################################################
Linux_B – Destination
===========================================================
## Hostname ##
sudo nano /etc/hostname
LinuxB
hostname LinuxB
hostname
sudo nano /etc/hosts
127.0.1.1 LinuxB
## Interface ##
sudo ifdown eth0
sudo ifconfig eth0 172.16.1.1 netmask 255.255.255.0
sudo ifup eth0
## Route (default) ##
sudo route add default gw 172.16.1.254 eth0
## Reverse/Remote SSH Tunnel ##
ssh -R 10002:localhost:22 lubuntu@172.16.1.254
######################################################
# This sets up the reverse/remote ssh tunnel
# between the destination (LinuxB) and the server
# in the middle (LinuxM) that will forward connection
# on the local port 10002 on LinuxM to the
# destination port 22 LinuxB via the established
# ssh session that has the reverse/remote tunel
# configured.
#
# After this command you will have the reverse/remote
# ssh thunnel configured and the bash/CLI of LinuxM.
#
# YOU MUST MAINTAIN THE BASH/CLI OF LinuxM ON LinuxB
# VIA SSH, FOR THE FORWARDING/TUNNELING TO WORK
#####################################################
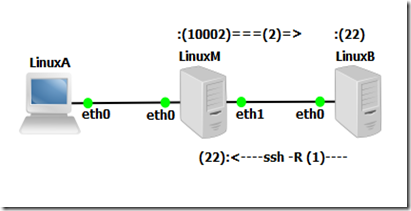
At this point you have this:
the reverse/remote ssh tunnel wating for a connection on LinuxM on port 10002 to forward LinuxB on port 22 (ssh)
Linux_A – Client
===========================================================
## Hostname ##
sudo nano /etc/hostname
LinuxA
hostname LinuxA
hostname
sudo nano /etc/hosts
127.0.1.1 LinuxA
## Interface ##
sudo ifdown eth0
sudo ifconfig eth0 192.168.1.1 netmask 255.255.255.0
sudo ifup eth0
## Route (default) ##
sudo route add default gw 192.168.1.254 eth0
## Connect LinuxM (will forward to LinuxB) ##
## Gateway Ports = ON on LinuxM ##
ssh lubuntu@192.168.1.254 -p 10002
or
## Connect LinuxM (will not forward to LinuxB) ##
## Gateway Ports = OFF on LinuxM ##
ssh lubuntu@192.168.1.254
ssh lubuntu@localhost -p 10002
######################################################
# Assuming the "Gateway Ports" is OFF, then the
# reverse/remote ssh tunnel will only be accessible
# on LinuxM locally
#
# So in the above commands we first connect via SSH
# to LinuxM, and from there connect local ports of the
# reverse/remote ssh tunnel so that it will forward
# the connection on the local port 10002 of LinuxM
# to the destination port 22 LinuxB
#####################################################
At this point you have this (Gateway Ports = ON):
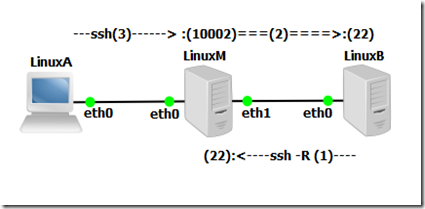 and you should be in the bash/CLI of LinuxB
and you should be in the bash/CLI of LinuxB ![]()
Related Links:
- http://www.marksanborn.net/howto/bypass-firewall-and-nat-with-reverse-ssh-tunnel/
- http://www.snailbook.com/faq/gatewayports.auto.html
1 comment:
great post , thank u for your blog visit us fiber optic solutions in dubai
Fiber optic network cabling
Post a Comment