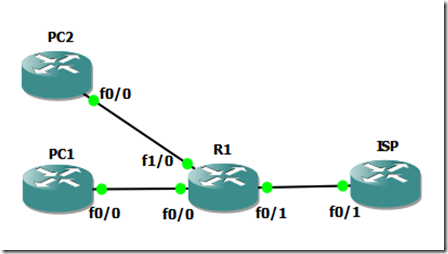
You have probably come across with this cenario:
where you want to forward the Public IP of R1 to PC1. To do this you just do a 1:1 NAT / Static Nat, and you are done.
The problem with this, is that you loose the management of R1, because all is forwarded to PC1.
Wouldn´t it be great if you could create an exception for the Telnet or SSH, port so that you keep managemnt of your router.
This is possible, basically you do the 1:1 NAT / Static Nat, and a Port Forwarding, to a Loopback on R1. This works because the Port Forwarding is more specific, so the port is forwarded to the Loopback of R1 instead of PC1.
The example bellow forwards the telnet port (23), to R1 Loopback Interface so that you can manage R1 it via Telnet.
Configs
## PC1 Config ##
hostname PC1
username cisco password 0 cisco
interface FastEthernet0/0
description *** LAN ***
ip address 192.168.1.1 255.255.255.0
no shutdown
ip route 0.0.0.0 0.0.0.0 192.168.1.254
!-- SSH Key Generation --
ip domain name cisco.com
crypto key generate rsa general-keys modulus 1024
line vty 0 4
login local
transport input ssh
## R1 Config ##
hostname R1
username cisco password 0 cisco
interface FastEthernet0/0
description *** LAN1 ***
ip address 192.168.1.254 255.255.255.0
ip nat inside
no shutdown
interface FastEthernet0/1
description *** WAN ***
ip address 203.103.3.110 255.255.255.252
ip nat outside
no shutdown
interface Loopback0
ip address 1.1.1.1 255.255.255.255
access-list 110 remark *** NAT ACL ***
access-list 110 permit ip 192.168.1.0 0.0.0.255 any
ip nat inside source list 110 interface FastEthernet0/1 overload
!-- 1:1 NAT / Static NAT --
ip nat inside source static 192.168.1.1 interface FastEthernet0/1
!—EXCEPTION – Fw Port 23 to Loopback0 - Telnet Access --
ip nat inside source static tcp 1.1.1.1 23 interface FastEthernet0/1 23
line vty 0 4
login local
transport input telnet
## ISP Config ##
hostname ISP
username cisco password 0 cisco
interface FastEthernet0/1
description *** WAN ***
ip address 203.103.3.109 255.255.255.252
no shutdown
line vty 0 4
login local
transport input telnet
Tests (on ISP)
## Check The Management of R1 via Telnet ##
telnet 203.103.3.110
Trying 203.103.3.110 ... Open
User Access Verification
Username: cisco
Password:*****
R1>
As expected we reach R1 via Telnet
## Check That The Other Ports Go to PC1 ##
ssh -l cisco 203.103.3.110
Password:****
PC1>
Another Cenario
If you want, you can have this scenario:
where instead of forwarding the Telnet port to R1 Loopback, you forward it to another equipment, in this case PC2.
The configs bellow build upon the configs above.
Configs
## PC2 Config ##
hostname PC2
username cisco password 0 cisco
interface FastEthernet0/0
description *** LAN ***
ip address 192.168.2.1 255.255.255.0
no shutdown
ip route 0.0.0.0 0.0.0.0 192.168.2.254
line vty 0 4
login local
transport input telnet
## R1 - Config (addon) ##
interface FastEthernet1/0
description *** LAN2 ***
ip address 192.168.2.254 255.255.255.0
ip nat inside
no shutdown
!—REMOVE: Fw Port 23 to Loopback0 - Telnet Access --
no ip nat inside source static tcp 1.1.1.1 23 interface FastEthernet0/1 23
!—EXCEPTION - Fw Port 23 to PC2 - Telnet Access --
ip nat inside source static tcp 192.168.2.1 23 interface FastEthernet0/1 23
Tests (on ISP)
## Check The Management of PC2 via Telnet ##
telnet 203.103.3.110
Trying 203.103.3.110 ... Open
User Access Verification
Username: cisco
Password:****
PC2>
As expected we reach PC2 via Telnet
## Check That The Other Ports Go to PC1 ##
ssh -l cisco 203.103.3.110
Password:*****
PC1>
Hope this was informative, and thant you for reading.