How to use 315Mhz RF Transmitter and Receiver Modules with Arduino
Description: This wireless transmitter and receiver pair operate at 315Mhz. They can easily fit into a breadboard and work well with microcontrollers to create a very simple wireless data link. Since these are only transmitters, they will only work communicating data one-way, you would need two pairs (of different frequencies) to act as a transmitter/receiver pair.
Note: These modules are indiscriminate and will receive a fair amount of noise. Both the transmitter and receiver work at common frequencies and don’t have IDs. Therefore, a method of filtering this noise and pairing transmitter and receiver will be necessary. The example code below shows such an example for basic operation. Please refer to the example code and links below for ways to accomplish a robust wireless data link.
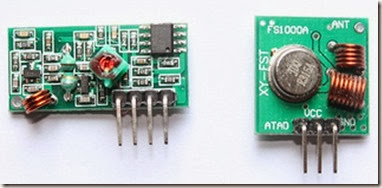
Module on the left: Receiver
Module on the right: Transmitter
Application environment
Remote control switch, receiver module, motorcycles, automobile anti-theft products, home security products, electric doors, shutter doors, windows, remote control socket, remote control LED, remote audio remote control electric doors, garage door remote control, remote control retractable doors, remote volume gate, pan doors, remote control door opener, door closing device control system, remote control curtains, alarm host, alarm, remote control motorcycle remote control electric cars, remote control MP3.
Receiver module parameters

1. Product Model: MX-05V
2. Operating voltage: DC5V
3. Quiescent Current: 4mA
4. Receiving frequency:315Mhz
5. Receiver sensitivity:-105DB
6. Size: 30 * 14 * 7mm
Technical parameters of the transmitter module

1. Product Model: MX-FS-03V
2. Launch distance :20-200 meters (different voltage, different results)
3. Operating voltage :3.5-12V
4. Dimensions: 19 * 19mm
5. Operating mode: AM
6. Transfer rate: 4KB / S
7. Transmitting power: 10mW
8. Transmitting frequency: 315Mhz
9. An external antenna: 25cm ordinary multi-core or single-core line
10. Pinout from left → right: (DATA; VCC; GND)
An example:
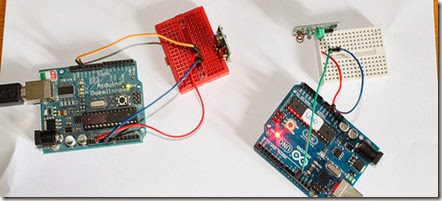
In this example, receiver and transmitter modules are connected separately to two Arduino boards. The transmitter data pin is connected to Pin 12 of Arduino and the receiver data pin is connected to Pin 11 of Arduino.
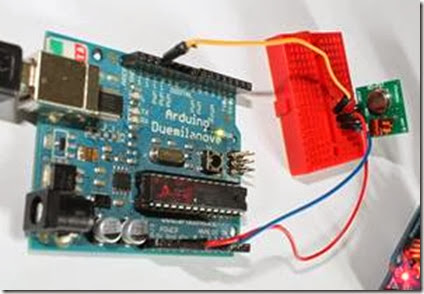
Data pin of transmitter module to Pin 12 of Arduino.
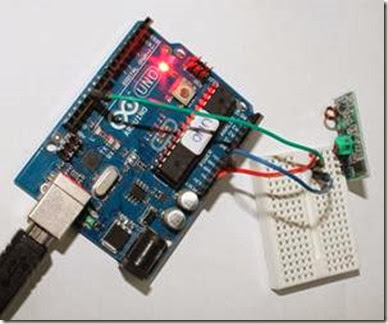
Data pin of receiver module to Pin 11 of Arduino.
Please note that there are two separate Arduinos for each module.
Connecting transmitter module to Arduino:
Sketch:
Download library(Virtual wire)
/*
SimpleSend
This sketch transmits a short text message using the VirtualWire library
connect the Transmitter data pin to Arduino pin 12
*/
#include <VirtualWire.h>
void setup()
{
// Initialize the IO and ISR
vw_setup(2000); // Bits per sec
}
void loop()
{
send("Hello there");
delay(1000);
}
void send (char *message)
{
vw_send((uint8_t *)message, strlen(message));
vw_wait_tx(); // Wait until the whole message is gone
}
Connecting receiver module to Arduino:
Sketch:
/*
SimpleReceive
This sketch displays text strings received using VirtualWire
Connect the Receiver data pin to Arduino pin 11
*/
#include <VirtualWire.h>
byte message[VW_MAX_MESSAGE_LEN]; // a buffer to store the incoming messages
byte messageLength = VW_MAX_MESSAGE_LEN; // the size of the message
void setup()
{
Serial.begin(9600);
Serial.println("Device is ready");
// Initialize the IO and ISR
vw_setup(2000); // Bits per sec
vw_rx_start(); // Start the receiver
}
void loop()
{
if (vw_get_message(message, &messageLength)) // Non-blocking
{
Serial.print("Received: ");
for (int i = 0; i < messageLength; i++)
{
Serial.write(message[i]);
}
Serial.println();
}
}
Download library(Virtual wire)
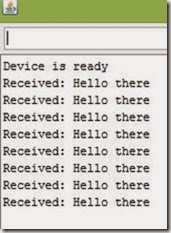
Output:
The transmitter sends a string “Hello there” and the receiver receives it and displays on serial monitor.
Vídeo Tutorial
Related links:
1. Virtual wire- Arduino Library
2. Buy 315Mhz receiver and transmitter modules on www.minibread.com
3. Video
- See more at: http://www.buildcircuit.com/how-to-use-rf-module-with-arduino/#sthash.ieHxO1DS.dpuf
Taken From:









![clip_image002[5] clip_image002[5]](http://lh4.ggpht.com/-wmn_Oj8PZe4/UqZnNPXJ0JI/AAAAAAAADf0/EZit80LWhi4/clip_image002%25255B5%25255D_thumb%25255B1%25255D.gif?imgmax=800)
![clip_image002[7] clip_image002[7]](http://lh5.ggpht.com/-Cyyp2PJenLM/UqZnO1wniZI/AAAAAAAADgU/soBOZ-02Ykc/clip_image002%25255B7%25255D_thumb%25255B1%25255D.gif?imgmax=800)

