How to Setup a VPN (PPTP) Server on Debian Linux
(also tested on the Raspberry Pi on Raspbian)
VPN-ing into your server will allow you to connect to every possible service running on it, as if you were sitting next to it on the same network, without individually forwarding every port combination for every service you would like to access remotely.
Using a VPN connection also has the upshot of, if desired, granting access to other computers on the network as if you where in it locally from anywhere across the internet.
While not the most secure of the VPN solutions out there, PPTP is by far the simplest to install, configure and connect to from any modern system and from windows specifically as the client is a part of the OS since the XP days and you don’t need to mess with certificates (like with L2TP+IPsec or SSL VPNs) on both sides of the connection.
Did i get you interested? then let’s go :)
Preface
- You will need to forward port 1723 and the GRE protocol (47) from the internet to the server to enable the connection (not covered here).
- You will see me use VIM as the editor program, this is just because I’m used to it… you may use any other editor that you’d like.~
Server Setup
Install the pptp server package:
sudo aptitude install pptpd
Edit the “/etc/pptpd.conf” configuration file:
sudo vim /etc/pptpd.conf
Add to it:
option /etc/ppp/pptpd-options
localip 192.168.1.5
remoteip 192.168.1.234-238,192.168.1.245
Where the “localip” is the address of the server, and the remoteip are the addresses that will be handed out to the clients, it is up to you to adjust these for your network’s requirements.
Edit the “/etc/ppp/pptpd-options” configuration file:
sudo vim /etc/ppp/pptpd-options
Append to the end of the file, the following directives:
ms-dns 192.168.1.1
nobsdcomp
noipx
mtu 1490
mru 1490
here we are assuming that we are editing the pptpd default options config and adding to it, but if for some reason you start with a black “pptpd-options”, you will need to enter those defaults (based on a “pptpd-options” on Raspberry Pi Runing Raspbian):
name pptpd
# BSD licensed ppp-2.4.2 upstream
# with MPPE only
refuse-pap
refuse-chap
refuse-mschap# Require the peer to authenticate
# itself using MS-CHAPv2
require-mschap-v2# Require MPPE 128-bit encryption
require-mppe-128
# Making the peer appear to other
# systems to be on the local ethernet
proxyarp# Debian: do not replace the default route
# with this you get split tunelling
nodefaultroute# Create a UUCP-style lock file for
# the pseudo-tty to ensure exclusive
lock# Disable Van Jacobson compression
novj
nobsdcomp# Turn off logging to stderr
nologfd
to get more detail on each item check a default “pptpd-options” file it’s has quite some detail on each item.
Where the IP used for the ms-dns directive is the DNS server for the local network your client will be connecting to and, again, it is your responsibility to adjust this to your network’s configuration.
Edit the chap secrets file:
sudo vim /etc/ppp/chap-secrets
Add to it the authentication credentials for a user’s connection, in the following syntax:
username <TAB> * <TAB> users-password <TAB> *
Restart the connection’s daemon for the settings to take affect:
sudo /etc/init.d/pptpd restart
If you don’t want to grant yourself access to anything beyond the server, then you’re done on the server side.
Enable Forwarding (optional)
While this step is optional and could be viewed as a security risk for the extremely paranoid, it is my opinion that not doing it defeats the purpose of even having a VPN connection into your network.
By enabling forwarding we make the entire network available to us when we connect and not just the VPN server itself. Doing so allows the connecting client to “jump” through the VPN server, to all other devices on the network.
To achieve this we will be flipping the switch on the “forwarding” parameter of the system.
Edit the “sysctl” file:
sudo vim /etc/sysctl.conf
Find the “net.ipv4.ip_forward” line and change the parameter from 0 (disabled) to 1 (enabled):
net.ipv4.ip_forward=1
You can either restart the system or issue this command for the setting to take affect:
sudo sysctl -p
With forwarding enabled, all the server side settings are prepared.
We recommend using a “Split Tunnel” connection mode for the VPN client.
A more in depth explanation about the recommended “Split Tunnel” mode, as well as instructions for Ubuntu Linux users can be found in the “Setting up a “Split Tunnel” VPN (PPTP) Client on Ubuntu 10.04” guide.
For windows users, follow the guides below to create the VPN client on your system.
PPTP VPN Dialer Setup on XP (split tunnel)
We will create a regular VPN dialer with one note worthy exception, that we will set the system to NOT use it as the “Default Gateway” when connected.
Skipping this step will limit the connecting computer’s surfing speed to the VPN server’s upload speed (usually slow) because all of it’s traffic would be routed through the VPN connection and that’s not what we want.
We need to start the connection wizard, so we will go to control panel.
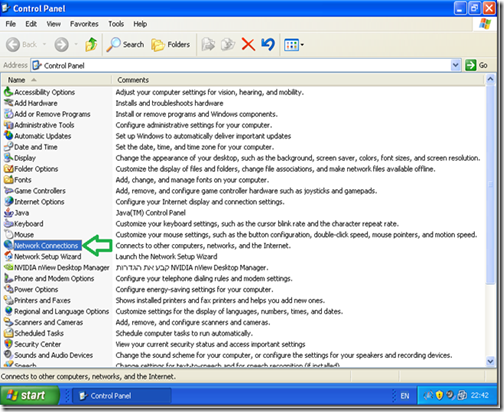
Go to “Start” and then “Control Panel”.
*If your system is setup with the “Classic Start Menu” you need to just point on the “Control Panel” icon and then select “Network Connections”.
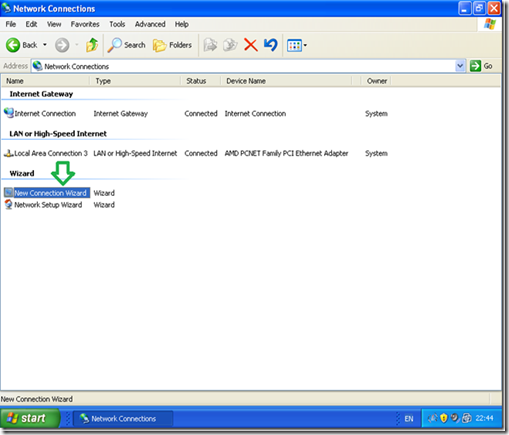
In “Control Panel” double click “Network Connections”.
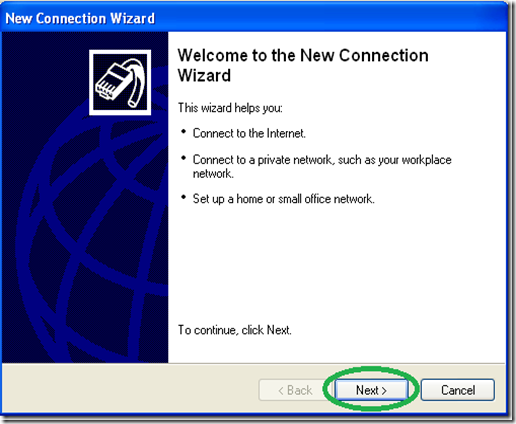
Double click “New Connection wizard”.
In the “New Connection wizard” welcome screen click “Next”.
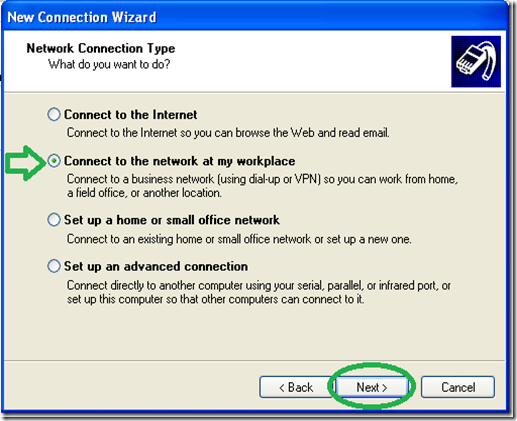
Select the “Connect to the network at my workspace” option and then “Next”.
Select the “Virtual Private Network connection” option and then “Next”.
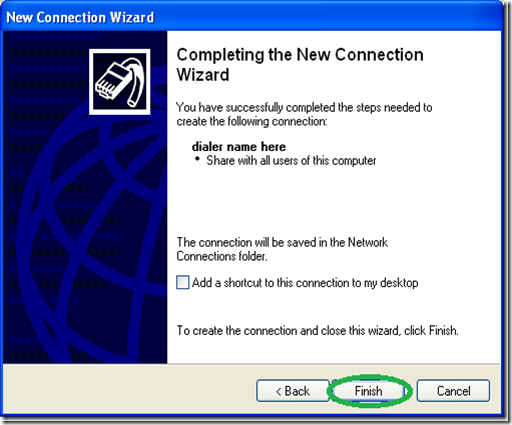
Give a name to the VPN connection.
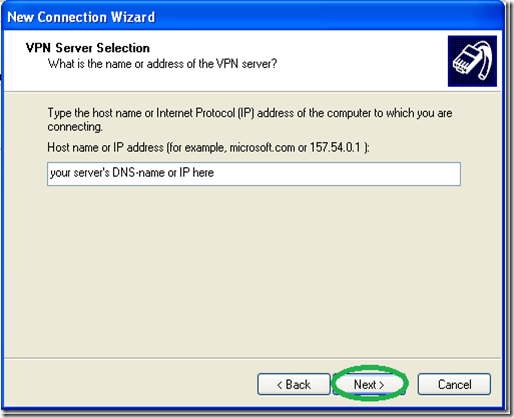
Type in the name of your VPN servers DNS-name or IP address as seen from the Internet.
Optionally You may choose to “Add a shortcut to the desktop” and “Finish”.
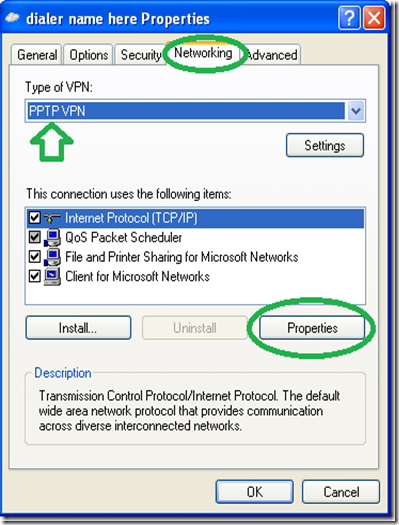
Now comes the tricky part, it is vitally important you do NOT try to connect now and go into the dialer’s “Properties”.
Go to the networking tab and change the “Type of VPN” to “PPTP VPN” as shown in the picture below (this is optional but will shorten the time it takes to connect) then go into “Properties”.
On the next window go into “Advance” without changing anything else.
On the next window, uncheck the “Use default gateway on remote network” option.
Now enter the connection’s credentials as you set them on the server and connect.
That’s it, you should now be able to access all the computers on your network from the XP client… Enjoy.
PPTP VPN Dialer Setup on Win7 (split tunnel)
We will create a regular VPN dialer with one note worthy exception, that we will set the system to NOT use it as the “Default Gateway” when connected.
Skipping this step will limit the connecting computer’s surfing speed to the VPN server’s upload speed (usually slow) because all of it’s traffic would be routed through the VPN connection and that’s not what we want.
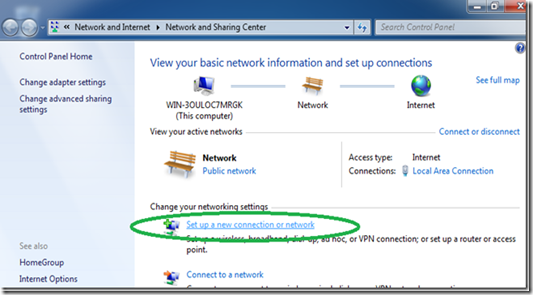
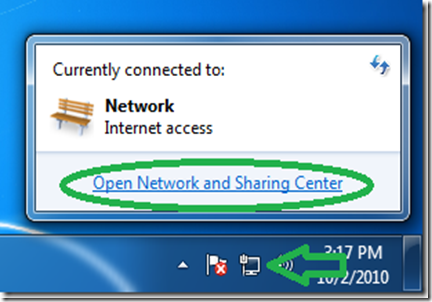
We need to start the connection wizard, so we will go to the “Network and Sharing Center”.
Click the network icon in the system tray and then “Open Network and Sharing Center”
In the Network center click on “Set up a new connection or network”.
Select “Connect to a workplace” and then “Next”.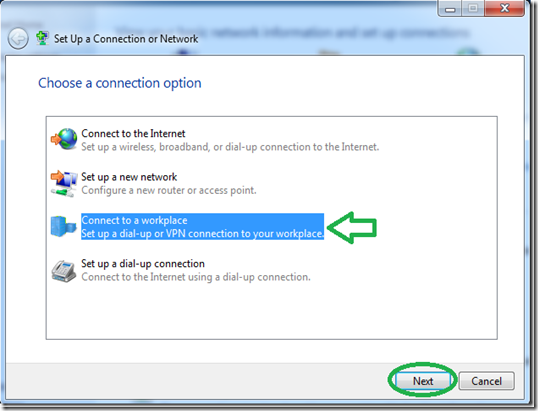
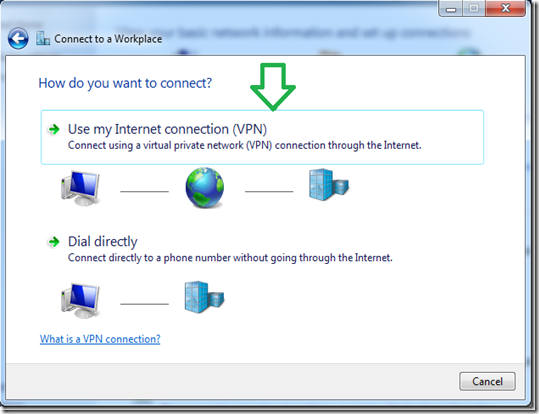
Click on the first option of “Use my Internet connection (VPN)”.
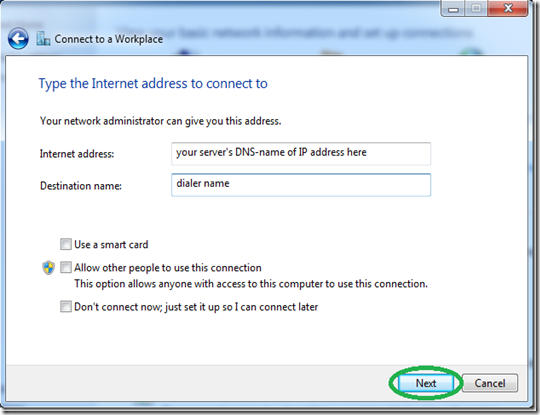
Set the address of your VPN server as seen from the internet either by DNS-name or IP.
Even though it won’t connect now because we stil need to go into the dialer’s properties, Set the username and password and hit connect.
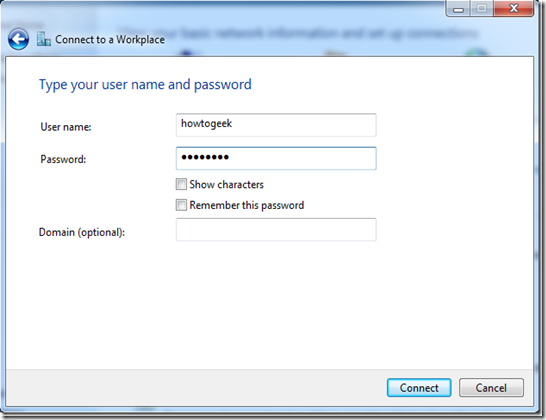
After the connection will fails to connect (that’s normal), click on “Set up the connection anyway”.
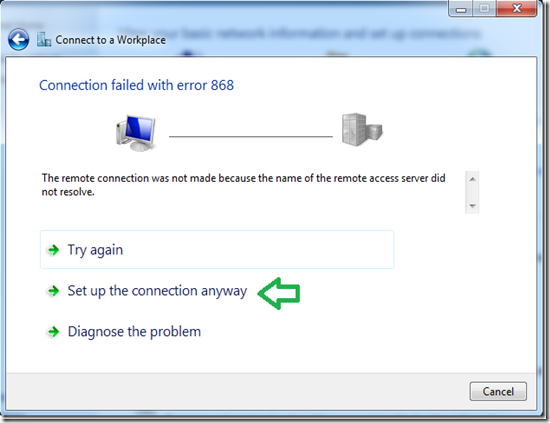
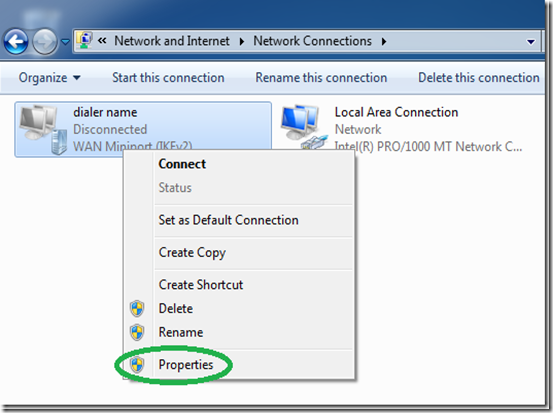
Back in the “Network Center”, click on “Change adapter settings”.
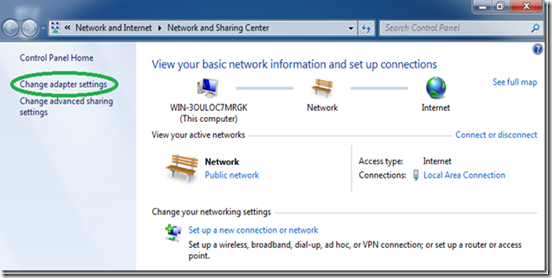
Find the dialer we have just created, right click it and select “Properties”.
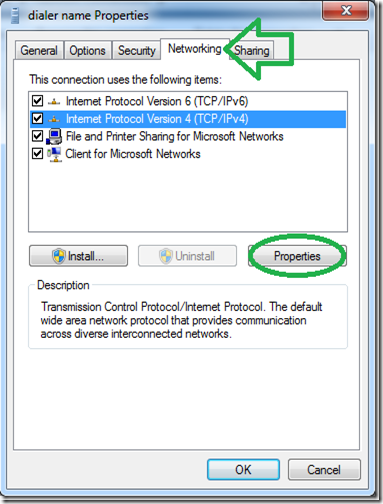
While its optional, for a faster connecting dialer, set the “type” of VPN to PPTP under “the “Security” tab.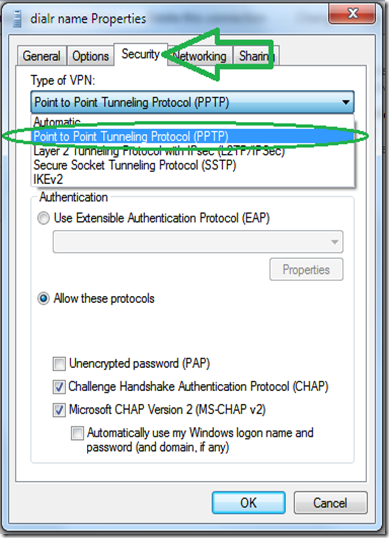
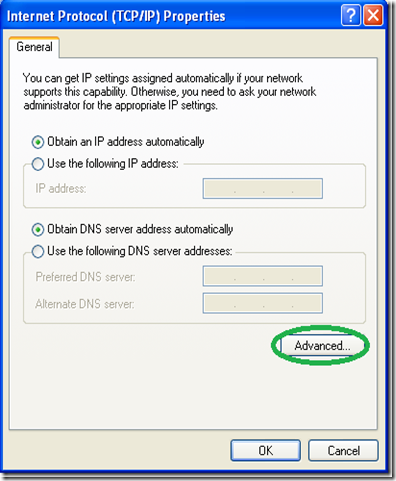
Go to the “Networking” tab, select the IPv4 protocol and go into it’s properties.
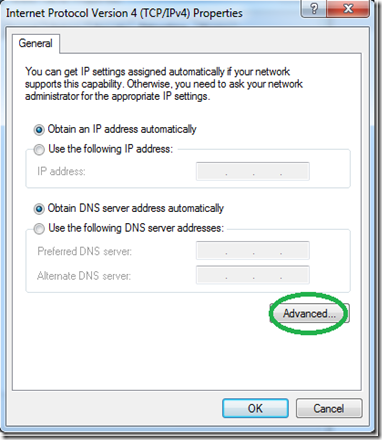
In the next window, click “Advance” without changing anything else.
On the next window, uncheck the “Use default gateway on remote network” option.
Now enter the connection’s credentials as you set them on the server and connect.
That’s it, you should now be able to access all the computers on your network from the win7 client.
Note: Be sure and read our guide to setting up a VPN client for Ubuntu Linux.
Based On; http://www.howtogeek.com/51237/setting-up-a-vpn-pptp-server-on-debian/








2 comments:
great post , thank u for your blog visit us fiber optic solutions in dubai
Fiber optic network cabling
THANKS FOR SHARING SUCH A AMAZING WORK
GREAT PIECE OF WORK!!!
structured cabling companies in dubai
Post a Comment