How to Setup a “Split Tunnel” VPN (PPTP) Client on Ubuntu 10.04
Sometimes you need to use a VPN connection to grant access to remote network resources and for that you use a VPN, but if you don’t want all of your client traffic to go through the VPN link, you’ll need to setup your VPN to connect in a “split tunnel” mode. Here’s how to do it on Ubuntu.
Note: make sure that you’ve read our article covering how to setup a VPN server for Debian-based Linux, which also covers configuring the Windows client.
Split what the what now?
The “split tunnel” term refers to the fact that the VPN client creates a “tunnel” from the client all the way to the server for “private” communication.
Traditionally the VPN connection is set up to create “the tunnel” and once it is up all the client’s communication is routed through that “tunnel”. this was good back in the day when the VPN connection had a couple of goals that overlapped and complimented each other:
- The connection was meant to grant access for the road warrior from anywhere.
- All of the client’s connections need to be secured by means of going through the corporate firewall.
- The client computer must not be able to connect a potentially malicious network with the corporate network.
The way the VPN connection of the time achieved this goal, was to set the “default gateway” or “route” of the client machine to the corporate VPN server.
- This method, while affective for the above goals has several disadvantages, espeshelly if you are implementing the VPN connection only for the “grant access” point:
- It will slow down the entire surfing experience of the client computer to the speed of the VPN server’s upload speed, which is usually slow.
- It will disable access to local resources like other computers in the local network unless they are all connected to the VPN, and even then the access will be slowed down because it has to go all the way to the internet and come back.
To overcome these shortcomings we will create a regular VPN dialer with one note worthy exception, that we will set the system to NOT use it as the “Default Gateway” or “route” when connected.
Doing this will make it so that the client will use the “VPN tunnel” only for the resources behind the VPN server and will access the internet normally for everything else.
Let’s get cracking
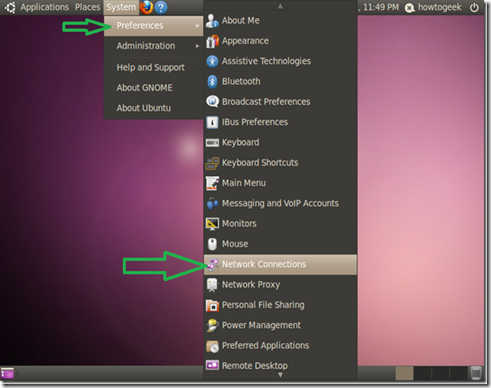
The first step is to get into “Network connections” and then “Configure VPN”.
One way you can do this is by clicking the desktop icon for networking as shown in the picture.
Another way is to go to “System” > “Preferences” > “Network Connections”.
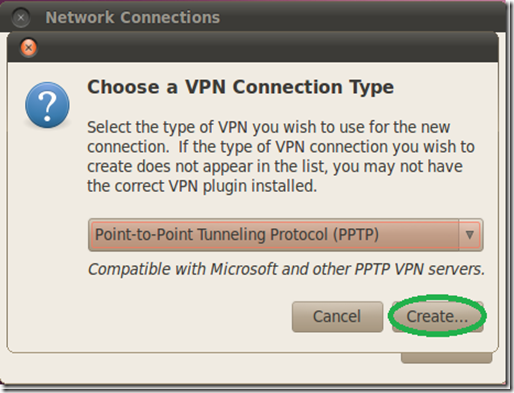
Once your on the “VPN” tab in the “Network connections” configurations window, click “Add”.
On the next window we only need to click “Create”, as the default connection type of PPTP is what we want to use.
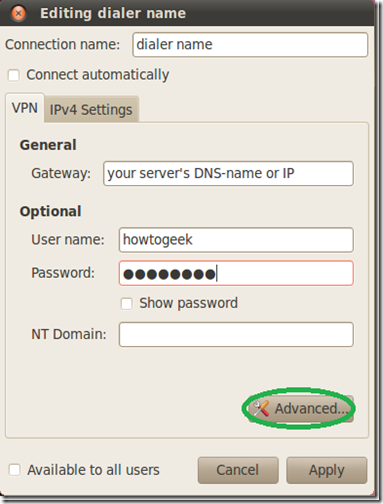
In the next window give your dialer a name, fill in the gateway with your servers DNS-name or IP address as seen from the internet and fill in the user credentials.
If you have used the “Setting up a VPN (PPTP) server on Debian” guide for the server setup or you are using this client for a DD-WRT PPTP server setup, you also need to enable the MPPE encryption options for authentication.
Click on “Advanced”.
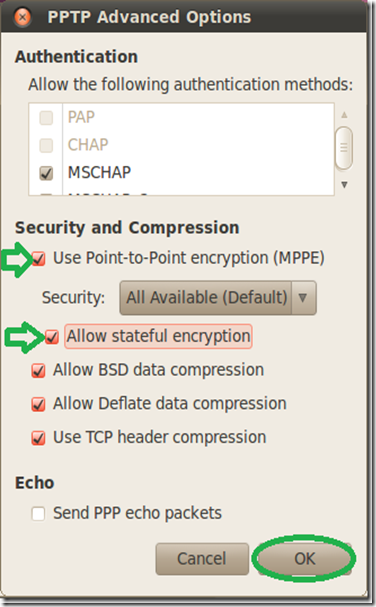
On the “Advanced Options” window check the first checkbox for the MPPE option, then the second checkbox to allow stateful encryption and click “OK”.
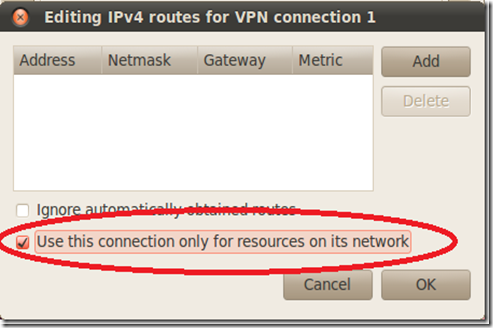
Back on the main window, click the “IPv4 Settings” tab.
On the routes configuration window check the checkbox of “Use this connection only for resources on its network”.
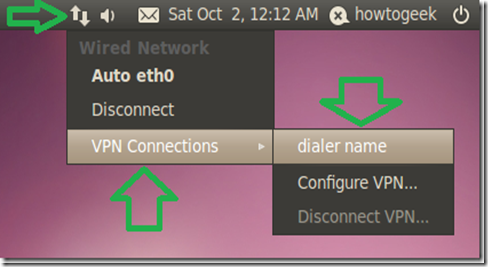
Activate the VPN connection client by clicking on the “Network connections” icon and selecting it.
That’s it, you can now access the resources on the VPN servers side as if you were on the same network while not sacrificing your download speed in the process…
Taken From: http://www.howtogeek.com/51340/setting-up-a-split-tunnel-vpn-pptp-client-on-ubuntu-10-04/



No comments:
Post a Comment